 |
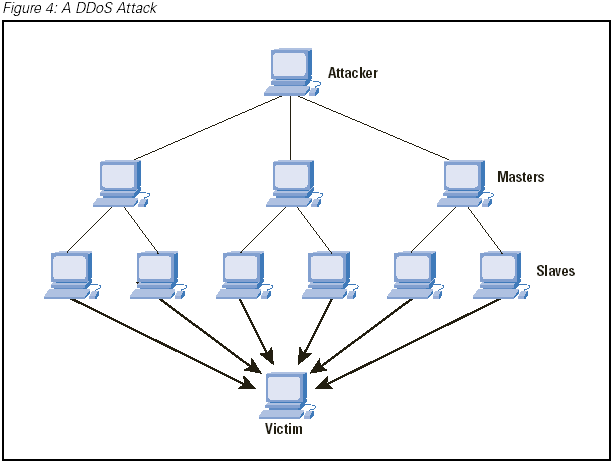
| The structure of DDoS attack. |
To put DDoS and DoS in laymen terms, DoS means that you have hired an army dirt and sand and all that shit (This represents the network) to block up the pipe (Bandwidth). By blocking the bandwidth, all users are unable to access your website as the bandwidth is guttered up with useless things that it is unable to send information over, meaning your website is down.
DDoS is instead one method of a DoS, and at the same time, DDoS is a much more common and advanced type of a DoS. We will start with a few older ones. These are the more common ones in the past and now.
Fragmentation overlap
By forcing the OS to deal with overlapping TCP/IP packet fragments, this attack caused many OSs to suffer crashes and resource starvation. Exploit code was realeased with names such as bong,boink, and teardrop.
How to defend yourself from such attacks...
The one way to ensure this will not happen is by securing your firewall and enforcing security on your connections.
Oversized Packets
This is called the "Ping of Death" (ping -1 65510 192.168.2.3) an a Windows system (where 192.168.2.3 is the IP address of the intended slave). What is happening is the attacker is pinging every port on the victims computer causing it to echo back 65510 requests. Another example is a jolt attack a simple C program for OS's whose ping commands wont generate oversized packets. The main goals of the "Ping of Death" is to generate a packet size that exceeds 65,535 bytes. Which can abruptly cause the slave computer to crash. This technique is relatively old and outdated.
How to defend yourself from such attacks...
Easiest way is just to update a patch to your operating system to overcome this problem.
How to defend yourself from such attacks...
Easiest way is just to update a patch to your operating system to overcome this problem.
Smurf Attacks
The smurf attack was one of the first to demonstrate the use of unwitting DoS amplifiers on the Internet. A smurf takes advantage of directed broadcasts and requires a minimum of three actors: the attacker, the amplifying network, and the slave. What happens is the attacker sends out spoofed ICMP ECHO packets to the broadcast address of the amplifying network. The source address of packets is forged to make it appear as if the slave system has initiated the request. Then all hell breaks loose!!! Because the ECHO packet was sent to the broadcast address, all systems on the amplifying network will respond to the slave. Now take a thought if the attacker sends just a single ICMP packet to an amplifying network which contains 500 systems that will respond to a broadcast ping, the attacker has now succeeded in multiplying the DoS attack by a magnitude of 500!
How to defend yourself from such attacks...
The best way to defend yourself from such attacks is through configuring your routers so they will not forward broadcast traffic onto your network from other networks.
How to defend yourself from such attacks...
The best way to defend yourself from such attacks is through configuring your routers so they will not forward broadcast traffic onto your network from other networks.
DDoS Attack (The most advanced and common once)
This is a much harder to block kind of attack, it has been used against big sites such as E-Trade, Ebay, and countless others. The problem with these attacks there very hard to trace. Most traces can link back to @Home users! The new DDoS attacks are termed Zombies or Bots. These bots rely heavily on remote automation techniques borrowed from Internet Relay Chat (IRC) scripts of the same name. A group of zombies under the control of a single person is called a zombie network or a bot army. The master of these armys or networks can do full fledged DDoS attacks or SYN floods. The basic estimate size of zombie networks are from a few systems to 150,000 systems. Even a few hundred machines could prove very dangerous.
- DDoS Script (Simple to Complex)
- Block IP's (This is usually done by using automated scripts as stated above, they are not easy to trace)
- Enforcing you firewall protection (This is a temporarily method)
Hope you enjoy this post and remember to comment, subscribe and share this with your friends !.
Comments appreciated!



















